With a simple Google account sign on, a Chromebook is quick to get you working, playing or whatever you want to do. But that Google account is the key to your Chromebook castle, and probably many other services as well, so you want to make sure it’s protected at all costs.
My podcast co-host, Matthew Miller found this out the hard way last week when he lost access to his Google account, not to mention many other accounts too. He has a full write up of what happened – he was SIM-jacked and lost his phone number not once, but twice, in just a few days – that I highly recommend you read.
We also discussed this as the main topic of our last podcast episode, if you’d rather tune in and hear about the experience:
Just to clarify what the root cause of this issue was: A nefarious person contacted Matt’s cellular provider – T-Mobile in this case – and impersonated Matt. They then got T-Mobile to move Matt’s phone number to their own mobile phone via the SIM card; likely saying they lost their phone and wanted to activate a new device and the SIM inside it.
Armed with Matt’s phone number and just knowing his email address, they then had the ability to reset his Google account password using the SMS-code 2FA that Matt had set on the account as a safety precaution. Essentially, they never had to know his Google password, they simply gained the ability to change it. And it all went downhill from there as Matt had stored personal data, bank account information and more on Drive. The hacker attempted to move $25,000 from Matt’s bank account but luckily, that transaction was reversed in time.
Obviously, this situation doesn’t apply only to a Chromebook since Google accounts are usable on nearly every platform and device. But I’m going to focus on the Chromebook aspect as well as provide tips on how to better protect your Google account.
Although Matt didn’t attempt to log in to his Chromebook during this fiasco, he probably wouldn’t have been able to. In most cases when you fire up a Chromebook, it’s going to connect to the web if possible. Had he booted his Chromebook, he wouldn’t have been able to sign in to it because the Google password associated with his account had already been changed. Aside from no access, other than with a Guest account, on the Chromebook, he would have also lost access to any locally stored data on the device.
For this reason, I specifically follow an approach of “if it’s important, don’t store it locally on the Chromebook.” I make sure that if my Chromebook is run over, lost or stolen, all of the important files are in the cloud. In fact, at the end of every day, I delete everything from the Downloads folder unless it’s important, in which case, I make sure it’s in the cloud. I even use a secondary cloud provider to store key information.
In terms of protection for my Google account and logging into my Chromebook, I use two-factor authentication or 2FA. However, I don’t use SMS codes for this because it’s the least secure option that Google provides.
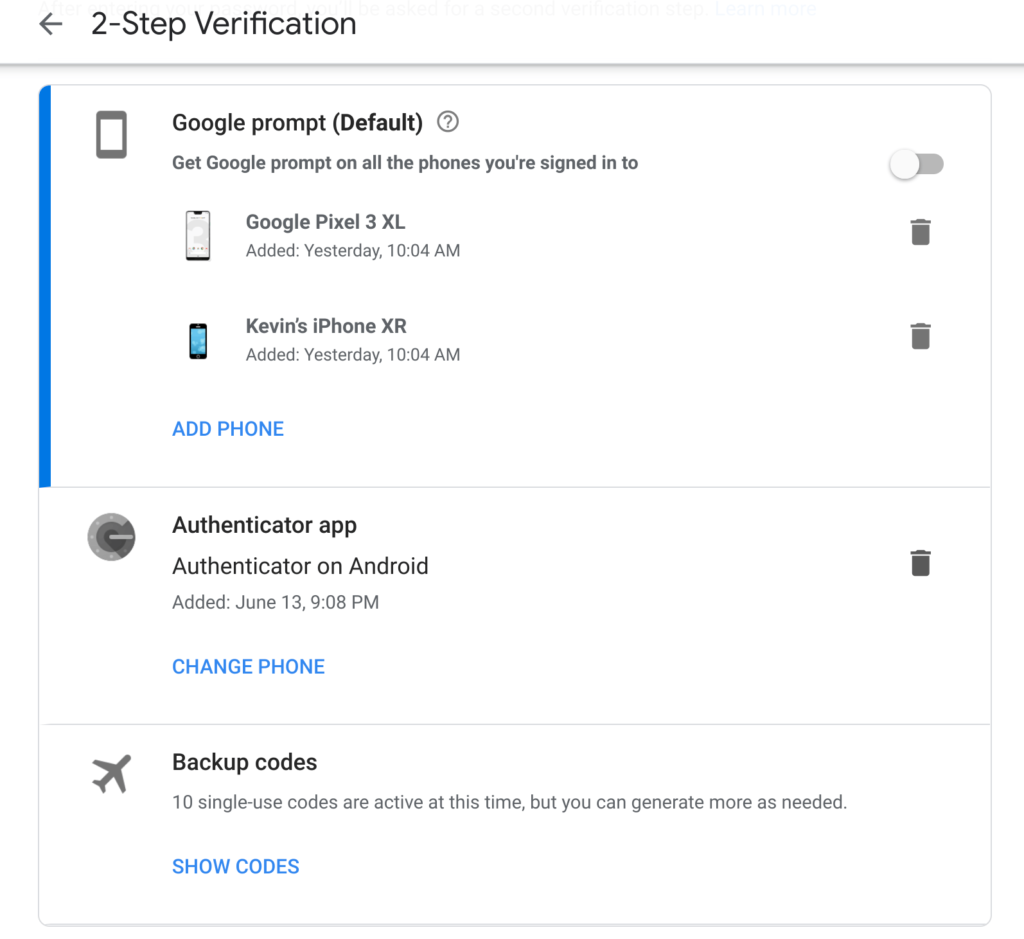
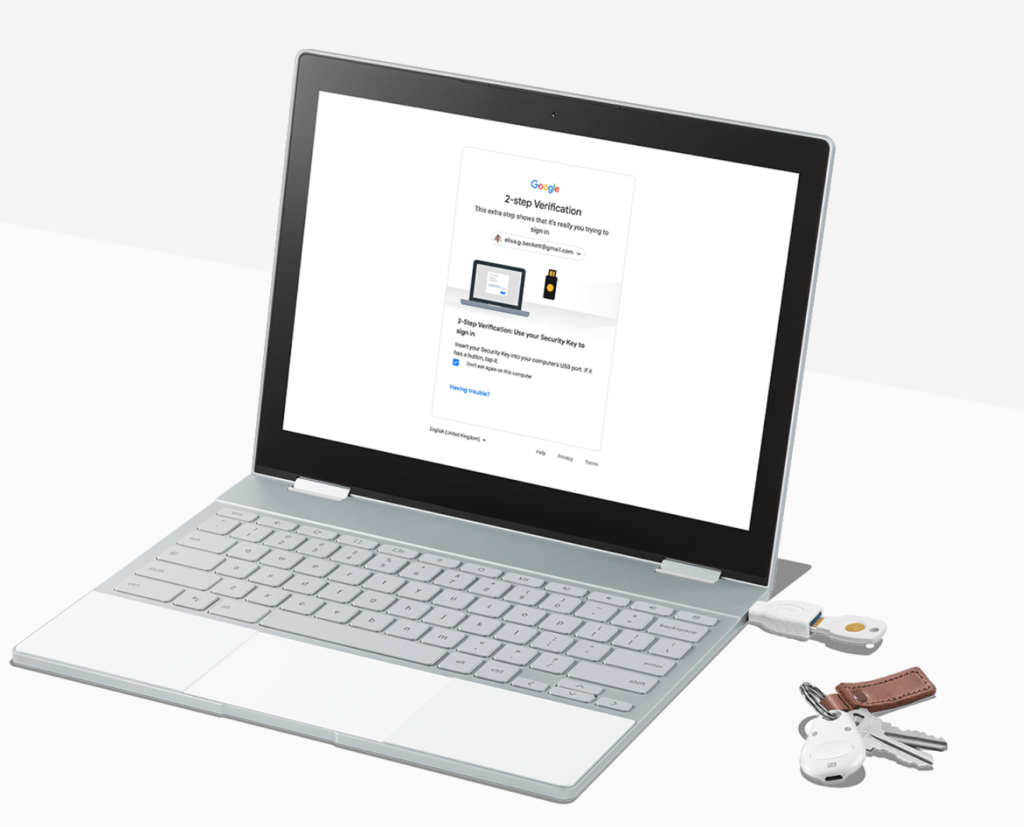
You can use the Google Authenticator app or if you have one, a USB key. I bought a Google Titan Security key for this purpose but I also use the Authenticator app for some of my accounts. Authenticator generates one-time codes that change every 30 seconds as the 2FA method. If you lose your phone, you can use one-time backup codes as well; I print these and keep them locked in a safe. Lastly, you can use a Google prompt on your mobile devices too.
Any or all of these methods should help protect your account, even in the case of your phone being stolen or your SIM is jacked.
But you can take this a step further on a Chromebook by setting up 2FA for your login. It’s a bit inconvenient but if someone actually does get your Google account password, they won’t be able to log in to your device. With 2FA on, you’ll be prompted for an authentication code, Google notification on a mobile device or your hardware key, depending on which you have set up, to complete the Chromebook sign-in process. Be sure not to click any options that say “trust this computer” when doing so if you want to get the prompt with every login on your Chromebook.
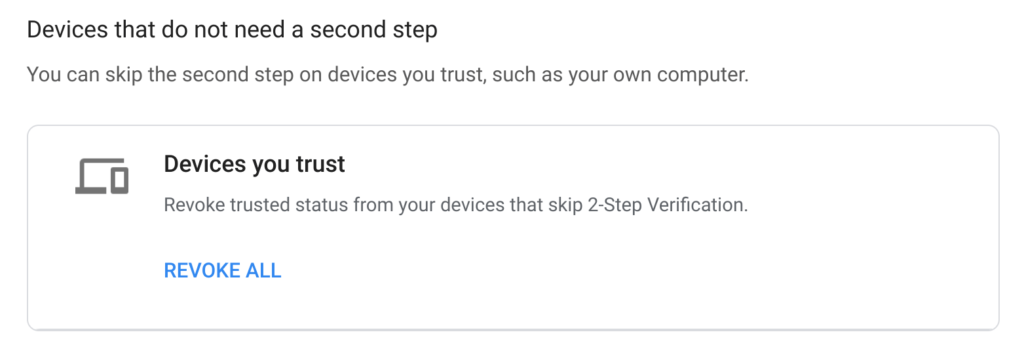
If setting up 2FA doesn’t seem to work with your Chromebook, you may have previously set it up as a trusted device. You can revoke that trust in the 2FA settings of your Google account:
Is it a pain to type in a code, hit an in-app prompt or carry a USB security key for every Chromebook log in? Yup. But I’d rather give up a little bit of convenience for a more secure account considering everything that a Google account or logged in Chromebook can access.


31 Comments
Make sure you also secure your recovery email accounts too. As you add security measures to your accounts, remove the least secure but make sure you have more than one 2FA fallback. Early on with 2FA I lost access to my phone. The ten one time passwords saved me. Review your account security regularly and remove unused access.
Great point! Matt had his own phone number and email in there; I switched both to my wife’s information.
So, now, I need your wife’s info to hijack your account…
I’m a bit surprised by this possibility of SIM jacking in the US. How comes the provider doesn’t have a more secure process? Would this be the price of convenience?
I love the idea of a key for our family main google account. My wife’s google photo app and my google photo app on our phones uses the main account so that all of our photos shoot up to the GooglePhoto library. Is this bad practice?
My other question is would the regular key (not titan) render her phone useless to the main account if I am using it or is it just a good backdoor to the account on top of 2factor?
In general I don’t think it is a good idea to share Google accounts since there is always the possibility one partner will do something that could impact both partners–for example, change a password. Better for each person to have their own account and then share whatever you want to share. It is very easy to share a Google Photos library with one other person. This also creates a “backup” of sorts for all the family photos since chances are you both won’t get locked out of your accounts or lose access at the same time.
I hear you. It’s the only way I can manage the photos because I have so many. I pay for 2TB of space for 10 bucks a month and the wife is only signed up to the google photos app as my account name on her phone so I capture everything. Any ideas how I can do the same thing and have my paid space still be the repository for photos between the two of us? I really am scratching my head on this one. I tried monthly migrating her photo up there but it is more automated this way.
You can Share photos between Google Accounts or within a family group. https://support.google.com/photos/answer/7378858
The the person who accepts the sharing invitation can go to settings and click “Save to your library.” I believe there is a limit of something like 20,000 photos that can be shared.
Note that if you use the High Quality setting in Google Photos you can save unlimited photos for free.
No arguments re: 2FA. However, how does this work if you access Google services from multiple devices in addition to the Chromebook? E.g., Phone, tablet, PC/Mac? Does every device used needs its own 2FA mechanism?
Same 2FA mechanism for the account works across all devices.
“Had he booted his Chromebook, he wouldn’t have been able to sign in to it because the Google password associated with his account had already been changed. Aside from no access, other than with a Guest account, on the Chromebook, he would have also lost access to any locally stored data on the device.”
“For this reason, I specifically follow an approach of “if it’s important, don’t store it locally on the Chromebook.” I make sure that if my Chromebook is run over, lost or stolen, all of the important files are in the cloud. ”
Huh? How does that protect your important files if you’re SIM-jacked?
I believe that the word “NOT” was omitted from that last sentence, and the fundamental premise of the article is flawed. You can protect access to your sign-in credentials, not your account. That is what the anecdote illustrates and it shows what NOT to do.
Service providers like Google, Amazon, Apple and Amazon do not authenticate users. They verify that user-created credentials are used. Accounts can be opened by anyone with internet access. How those accounts are managed by the services, who has access, if and how they are screened, trained and managed are unknown. Liability to the users? None except by suit. There is no equivalent to the FDIC to protect consumers with paid service accounts.
That is security by obscurity, service without accountability. If you knew a bank worked that way, would you keep your money there? Why your financial information?
A Google account cannot be secured or protected by a user. There is no difference between “hoping to protect one” and “helping to protect one”. It’s wishful thinking.
As far as sign-in credentials, if you can’t sign into Google, you can not access your Drive data. If someone has control of your Google account, they have control of every other service which has credentials saved/stored/synced with your Google account. That would argue for NOT using Drive or any cloud service for storing important data, unless you need to manually log in every time that you access that storage with something that cannot be lost or stolen, and which cannot be copied.
The example of a Google account being compromised through a cellphone illustrates the problem with a “security system” having too large an attack surface. While it is convenient to have single sign-in, every device that uses that sign-in is a point of vulnerability.
The “solution” to hardware based security is to have all the components of a system be secure, authenticated devices with secure authenticated communication links. NO consumer system today provides this.
An external hardware token device like a Yubikey is not a solution, it is a physical encumbrance. MFA that uses a mobile phone that can be cloned with SMS or email is a complexity, but not a solution. These “systems” are not secure by design, but patches applied to a fundamentally insecure system.
If you want your data to be safe, secure and recoverable, access control needs to be where it is secure, perhaps in your head, but not on a mobile device or in the cloud.
I’ve tried using Google Authenticator but it never works so I still use SMS but put a Pin on my phone account. So how is anyone going to find out my phone number anyway?
Truepeoplesearch.com, actually. I had my biological grandfather’s name, searched him on that website, and found a list of phone numbers of his. I just started calling them until I got an active number (which was his).
It was really easy.
OMG, that’s pretty scary except it only lists land lines which are not any use to anyone.
I use Google Authenticator (or Authy) daily, and have never had a problem. I also use a Yubikey, but it cannot be used on every site or app.
I was checking my 2FA on Google. I have the new Pixel 3A XL phone and now says I can it to my account.
How safe is the security key in the phone compared to using my Yubikey?
Brad
I’m not sure if this would help or not, in this instance, but since signing-up for Google Voice, that’s the only number I give out (other than family). Pretty sure T-Mobile’s response would have been, “….eh, that’s not a real number.”
Wonder how Google Fi would have handled it?
Thanks for very good post. However, I do not think the paragraph that begins with the following sentence makes as much sense as the others: “For this reason, I specifically follow an approach of “if it’s important, don’t store it locally on the Chromebook…”
Following that policy would not have protected Matt from his security/information breach. To be sure, in the particular case of Matt that you discuss at length, the reverse could have been true. (*The information and files exposed in Matt’s case were precisely that information and those files stored in the cloud in his accounts.*) In any case, a remote access hack is technical and technically much more difficult than the social engineering hack that you described against Matt. Just to be clear, the social engineering hack against Matt would not have provided access to information and files stored offline in folders on his computer and that hack would only have provided access to information and files stored online in the compromised accounts. The sim hack counts as a social engineering hack. What devices that sim hack further compromises depends on the particular connections between accounts on the sim device and accounts on other devices. Apart from outright stealing/gaining physical access to a device (which is the crudest kind of hacking if it counts as hacking at all), although some people might want to protect data stored on a device, it is not so clear that the reasons for wanting to do so follow from the previous paragraph when you typed, “For this reason, I specifically follow an approach of “if it’s important, don’t store it locally on the Chromebook…”
Peace.
Of course, this assumes Google follows their own rules. I changed phone numbers and despite not using SMS authentication Google decided to use that method to make sure it was me logging in. They had my old phone number stored as a backup phone, which I had forgotten to change. No matter what I did I was unable to get Google to let me use the prompt, or the authenticator app, or the one-time codes. Google also decided several “trusted devices” were no longer trusted. This all happened not when traveling, but in my own home. I was finally able to login from work where my phone once again was recognized as a trusted device.
Kevin the issue with Matt’s scenario seems not related to 2FA… to use 2FA you need to have the account password which the hacker didn’t.
The issue is with the recovery settings in case of password lost etc… where you only have 3 options (as far as I can see). Phone number (dangerous as witness by Matt), another email account or a security question (not too secure in my mind as well)
You cannot use authenicator or physical key or backup codes as recovery backup…
In fact, this issue seems to show the disadvantage of 2FA because of the use of your phone number for SMS codes and/or the recovery number. If instead a person had just a username and a decent password and no recovery phone it wouldn’t have happened. I’m not arguing against 2FA. But for many sites your phone number remains an Achilles heel. Using someone else’s phone number is sure to cause problems. What happens when they change the number without telling you? Or you are in Australia and you need a SMS code from someone sound asleep in New York?
One thing has always confused me about these SMS code attacks. If I have Google Prompt set up as my default 2FA, Authenticator as a second backup, and then SMS and Backup Codes as additional options, what is to keep someone who gained access to my phone number and knew my email address from resetting my password by simply continuing to click on “Try another way” at the password field until they get to the SMS code option even though it’s not the default. Is the only way to make the account secure to completely remove SMS codes as an option and limit myself to only three ways?
In my experience, you have to remove BOTH SMS as a 2FA option and a phone number as an account recovery option. As I stated above, despite only having my phone number as an account recovery option Google for some reason decided that the only way I could login was having an SMS code sent to my recovery phone. When I clicked “try another way” I was only given the option to have the SMS sent to my old phone number, no longer in service. Maybe that was just a bug, but it indicated to me how tied to our phone numbers life has become, and despite all of our best preparations for security there are always holes we can fall into.
Important! I just listened to the discussion about this in MobileTechRoundup #472 podcast.
In conjunction with the fortunately aborted attempt to steal $25,000 from Matt, he mentioned the bank suggested the transaction would go through and be funded by his “Overdraft on his Credit Card.”
“Overdraft protection” is a huge banking industry consumer rip-off. Imagine not only having $25,000 stolen, but having to pay it back to the bank at a high rate of interest. Go into your bank accounts, and turn “Overdraft Protection” off. It is far better to pay a bounced check fee than find yourself in debt to your bank because it blessed you with “Overdraft Protection” when a criminal transfers money out of your account.
Data in the cloud: can we say “Duh?” Matt and Kevin, you’re both geeks. It is reasonably safe to store data in the cloud if you encrypt it locally with a good encryption program and password before moving to the cloud. 7-Zip is available on Windows, Linux, and Mac (Keka on Mac). It does not seem to be available on iOS but is on Android which may be the path to use it on ChromeOS (Linux on a Chromebook is another).
Same for all those documents in the “Iove you letter.” Put them in a password manager, e.g., the free and excellent KeypassXC. Use a good KeypassXC password and your password files can be stored in the Cloud, though I recommend keeping them locally only.
Despite all this valid discussion about how to secure cloud accounts I am convinced that storing everything in the cloud is far, far more secure for most people. Yes, geeks here are disciplined and organized enough to properly utilize multiple layers of backups, including local and cloud, and encryption, but 99% of the computer using public is not. I have assisted many friends and even co-workers who did not have any sort of backup in place, cloud or local. And, even if they do, it is often set up incorrectly and barely secured with terrible passwords and physical security. Most phones I see are unlocked and ready to steal. It is a wonder more people aren’t hacked daily, though probably the biggest danger to most is losing their data due to human error or hardware failure. I have personally had multiple computers and remote hard drives fail, and all it takes is one fire, flood, or major power outage and your previous local backup is toast.
Toward the end of the podcast Kevin correctly notes passcode stolen or forgotten locks the user out of local storage on a ChromeOS device. True, that’s Google’s initial ad for Chromebooks. Stolen, lost in the river, your data is safe in the cloud. But there’s Matt, locked out of both device and cloud by a password thief.
Local backup of critical files is basic.
There’s also Google’s Advanced Protection Program. https://landing.google.com/advancedprotection/
Thanks, John. Spent some time yesterday “hardening” Google accounts. Found there are some differences between free GMail accounts and GSuite. A potential weak point is payment for the GSuite accounts I manage goes through card attached to free Gmail, and that’s also the recovery email.
That recovery question “first date of account” isn’t available to even logged in users. If, like me, you’ve ha an active Gmail from the beginning of Gmail, and pruned thousands of old and inactive emails, that date’s just not available. As one angry post on Google support complained, why would Google use an unanswerable question?
Google should be more proactive and tell people to make a note of when they first signed up for the account. I was able to find that by searching for and finding emails from Google when I first signed up. Another possibility might be asking a friend or relative to search for the earliest email from you sent from Gmail. My son had one I sent as a test when I first signed up. I have also removed my phone number as both an authentication option and as a recovery option. I have a recovery email address with another service that is also pretty well hardened. I periodically use Takeout to download all my Gmail, files, and photos to be stored on local hard drives, though there would be gaps if I lost my actual account.
I have a Pixelbook, obviously previously set up for my account. I just got a new Titan Security Key bundle and I cannot figure out how to force my Pixelbook to require providing my Titan key (either BT or USB) on log in even though I have them configured for 2FA in settings. No matter whether I enable just password or password & pin, I never get prompted to provide the second factor. Documentation is awful and frankly this article is not very specific either. Need something very step by step to troubleshoot.
I don’t think this is available with consumer level accounts and I’m not necessarily sure you get this with GSuite or not. If you powerwashed your CB, when you first go through setup, you would be prompted for your key. After that, you only need your key for your Gmail login. If you log out of your Gmail account and log back in you will be prompted. One thing to be aware of is that there is a “Don’t prompt me” checkbox that I always need to uncheck to force requiring the key at every Gmail login. It has been this way for years. I have no idea why one would want to disable this security feature.?????
Also, I don’t believe the Titan Bluetooth key works with Desktops or Chromebooks. I had hoped this would work with my CB but I think it is strictly Android Phones.
If you are using another Gmail account as your account recovery email, make sure you also add the key to that account as well. Make sure you have at least backup codes as a redundant 2fa method.
I should add that the Titan BT key does work with a Chromebook, but only if attached by the USB cable.